Advanced Endpoint Protection and Incident Response Services
Advanced Endpoint Protection and Incident Response Services
Prevention by Deception
Empower Your Security: Explore Advanced Endpoint Protection and Incident Response Services at Delphi Infotech for Robust Cybersecurity Solutions.
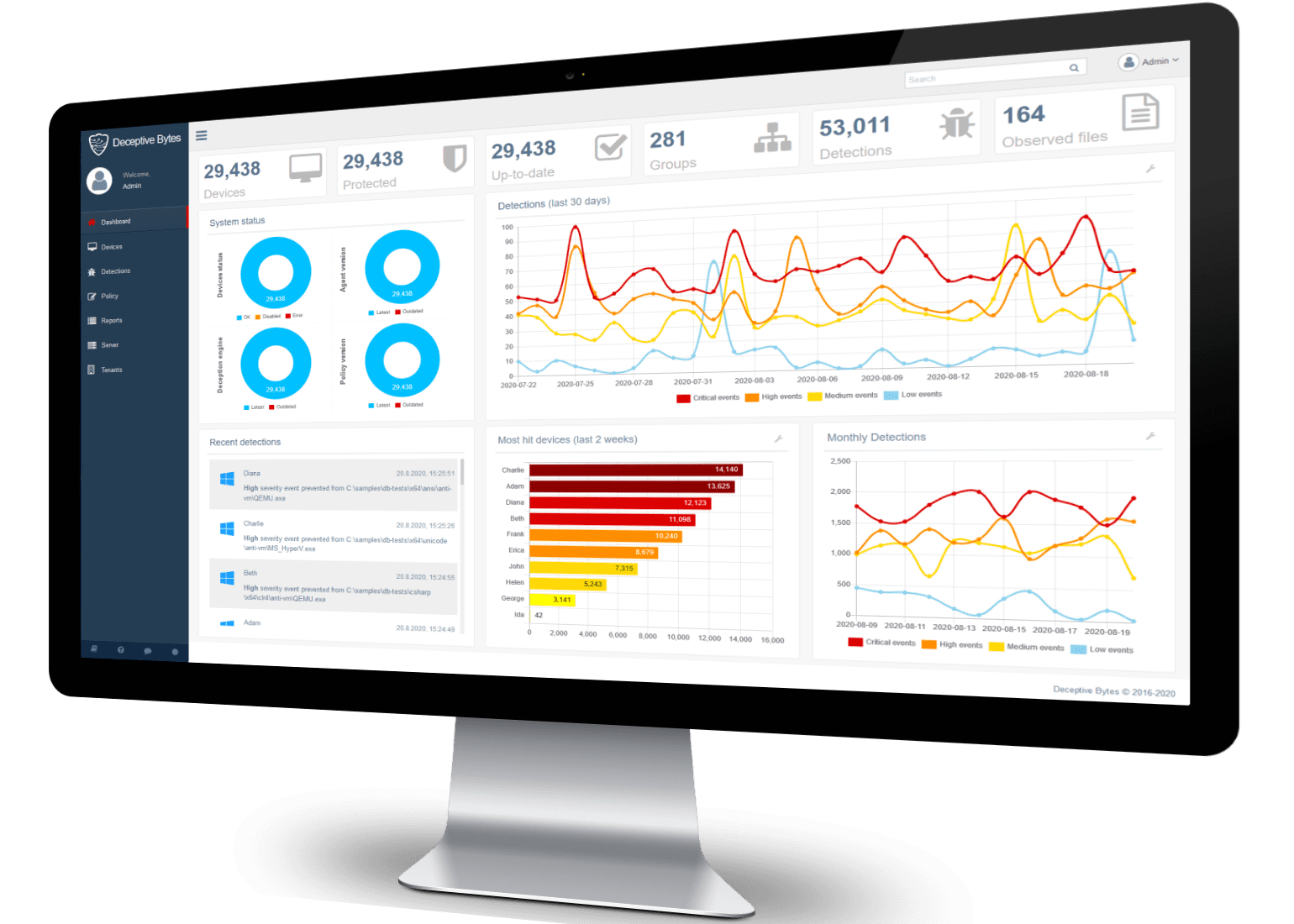
Understanding Endpoint Detection and Response.
Enhance your cybersecurity posture with our cutting-edge endpoint detection and response (EDR) services. Gain real-time insights into potential threats, swiftly detect malicious activities, and respond proactively to safeguard your digital assets. Delphi Infotech provides comprehensive EDR solutions to fortify your defense against evolving cyber threats.
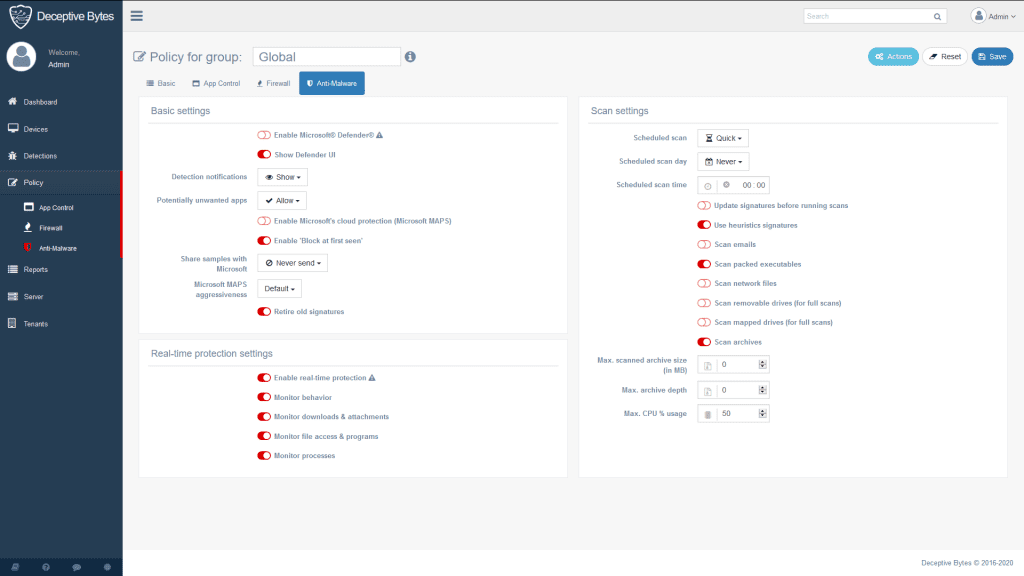
Preventing and Managing Malware Attacks.
Protect your organization from the ever-looming threat of malware attacks with Delphi Infotech's advanced endpoint protection. Our tailored solutions go beyond conventional methods, employing proactive measures to prevent malware intrusions. In the unfortunate event of an attack, our incident response team is ready to swiftly contain, analyze, and mitigate the impact, ensuring minimal disruption to your operations.
USES MALWARE'S DEFENSES AGAINS IT
USES MALWARE'S DEFENSES AGAINS IT
Shaping Attackers Decision Making
Deceptive Bytes provides an innovative solution against threats in enterprises’ most critical and exposed assets, their endpoints!
The solution is a fully endpoint-centric prevention/deception platform that creates dynamic & deceiving information, responds to the evolving nature of advanced threat landscape and interferes with attackers attempts to recon the environment that deters them from executing their malicious intents, through all the stages of compromise in the Attack Kill Chain – covering advanced & sophisticated malware techniques, constantly making sure all the endpoints & data in the enterprise are secured.
PREVENT NEVER-SEEN-BEFORE CYBER-ATTACKS
PREVENT NEVER-SEEN-BEFORE CYBER-ATTACKS

Providing multi-stage protection through the Endpoint Kill Chain
ADVANTAGES
Simple, Effective!
EFFECTIVE AGAINST
One Agent To Protect IT All
Leave your details below and our program advisor will get in touch and guide you about the products, rates and any other questions you may have.