Prevention Starts with Perception.
AI-powered email, web browser, and cloud apps security.
ONE platform. ALL threats. Lightning fast. Zero overhead.
Fortify Electronic Mail Security
Prevention Against Intrusion Attempts
Combatting Phishing and Spear Phishing
Rapid detection, investigation, and remediation of all attacks across email, web browsers, and cloud collaboration channels. We prevent phishing, ransomware, BEC, ATO, spam, malware, Zero-days, and N-days well before they reach your end-users.
Effective Threat Prevention
Consolidate your complex existing security stack and your point solutions – including AVs, sandboxes, CDRs, RBIs – with one effective solution against APTs, phishing, BEC, ransomware, malware, ATO, impersonation attacks, and spam.
Multiple layers of static and dynamic engines, including advanced AI/ML, next-gen sandboxing and patented web browser security technology prevent malicious files, URLs, and social-engineering based techniques.
Top Attack Vector Coverage
Detect, investigate, and remediate threats across email, web browsers, cloud storage, CRM, instant messaging apps, or any cloud application with one solution, viewed from one intuitive dashboard. Add new channels in one-click to provide threat detection coverage across all apps.
Managed Incident Response. A SOC Multiplier
Deployed within minutes, with zero fuss to your IT team. You receive a managed service that conforms with any existing policies and SIEMs. No need to change MX record for email security, or deploy a new customized browser on your endpoints.
A fully managed Incident Response service supercharges and optimizes your SOC team’s performance; eliminating false negatives and reducing false positive to bare minimum; analyzing, investigating, and rapidly remediating attacks.
Agile, Fast & Responsive
Near real-time scan speeds ensure no delays in receipt, regardless to scale and traffic volume. Cloud-based architecture shortens development and deployment cycles as new cyber-attacks techniques emerge, ensuring you’re at least one step ahead of attackers.
WHY PERCEPTION POINT
SOLUTION OVERVIEW
SOLUTION OVERVIEW
On top of providing the best detection rates in the market, we are committed to act as your trusted advisor, helping security experts and IT managers to better intercept, analyze, and understand any attack.
OUR SERVICES
OUR SERVICES
Our 360-degree framework is comprised of a complete stack of added-value services, covering the everyday needs of the modern SOC, IT, and Security teams.
Incident Response
The X-Ray
Reporting
End-user Reporting
Auto-deployment & Updates
Support
Incident Response
Incident Response
MACHINE LEARNING, AUTOMATION, AND CYBER EXPERTS ACT AS YOUR SOC MULTIPLIER
Your security team faces a growing amount of challenges. Between monitoring content traffic, analyzing incidents, managing false positives, interacting with end users, and learning about new attack trends, your team is posed to face burnout. Perception Point’s Incident Response Service is here to solve these problems for you.
Combining machine learning capabilities, automated processes, and close interaction with our cyber analysts, we make sure every incident is analyzed, creating a safe content-sharing environment.
Identify and Reduce
Cyber Risk
Ongoing review and analysis of all incidents flagged by Perception Point’s solutions. Identifying new phishing, BEC, and other content attack patterns and real-time response to block active campaigns against any organization at any time.


Business Streamlining
(the “Where is My Email?!” issue)
Instead of spending hours searching for important data and releasing it from quarantine, your team can count on us. Our Incident Response tools and supporting team review all suspicious content and releases the incidents that are actually safe, before your users even notice. The result: virtually ZERO false positives.
“Phone a Friend”
Your team deals with overwhelming types of threats from different channels. With a unique “Request Investigation” capability, your experts gain unprecedented access to our cybersecurity analysts who will help your security team protect your organization with just a click of a button. Imagine a full professional report for any of your requests.

The X-Ray
The X-Ray
THE ULTIMATE SOC OPERATIONS TOOL
Personalized “viewer” helps security and IT experts to see, understand, and manage each and every incident in the most detailed way.
Insights
See most targeted software, URL & file classifications, most targeted users, and more. Understand full attack paths and, why content was marked malicious or clean.
Analyzer
Encountered a new file or URL from other channels not protected by Perception Point? No worries – simply upload any suspicious content piece, from any software, and get an immediate analysis. Literally drag and drop.
Manage Policies and Rules
Simple, easy-to-use widgets help you implement, manage, and update new policies. Imagine a full set of rules all in one place.
Conduct Forensics
Determine the scope and scale of an attempted attack. Identify current threats and prioritize response efforts.
Reporting
Reporting
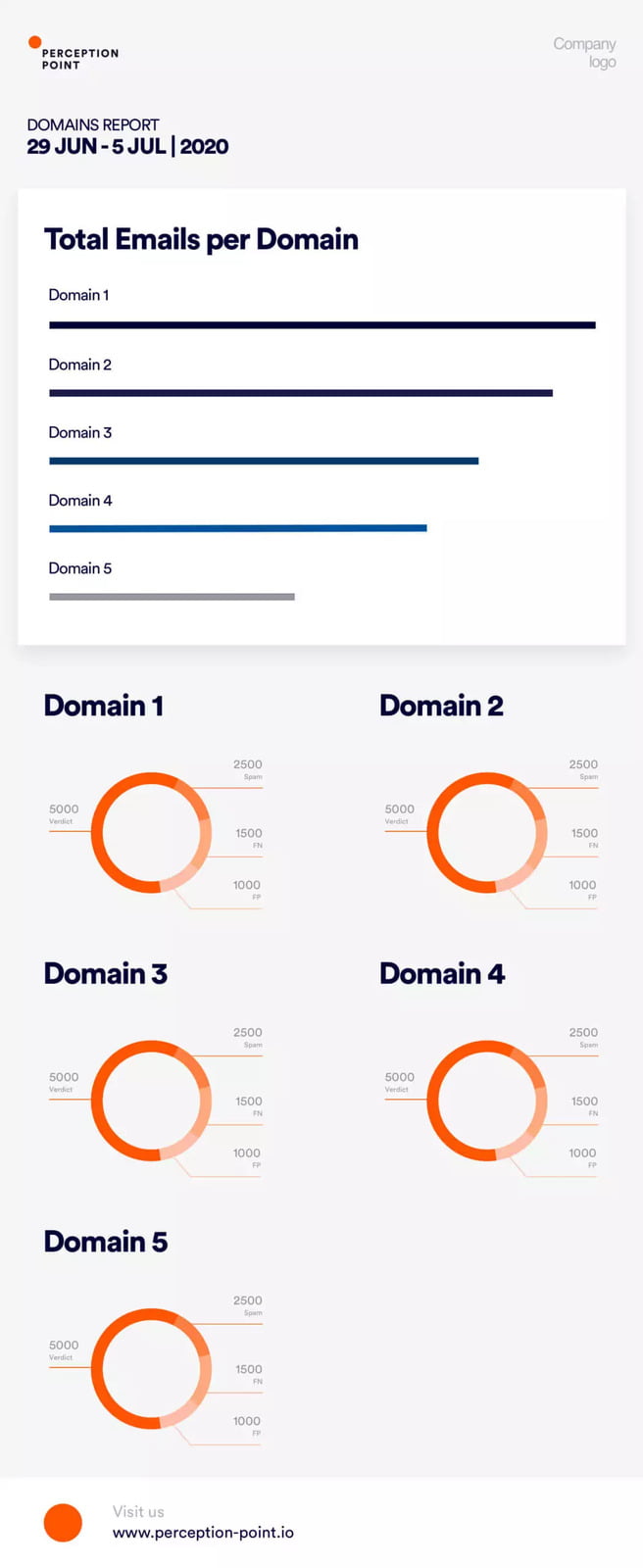
CUSTOMIZED REPORTS WITHIN A CLICK REACH
Unique interface enables any type of user – CISO, IT Manger, Email Manager, Security Analyst – to control the level of depth of interaction with our system. Strong filtering and search capabilities enable to export any requested data, allowing you to analyze it in your preferred application.
Perception Point offers various types of reports:
IR reports
Ad-hoc incident reports on unique incidents, daily digests for VIP clients, and weekly/monthly reports on attack trends.
Customized reports in just a click
Exporting any set of data from the hundreds of data points collected automatically by the system, at your discretion.
Scheduled concierge reports
Weekly, monthly, and quarterly reports, including aggregated summaries of all activities and trends based on real life data.
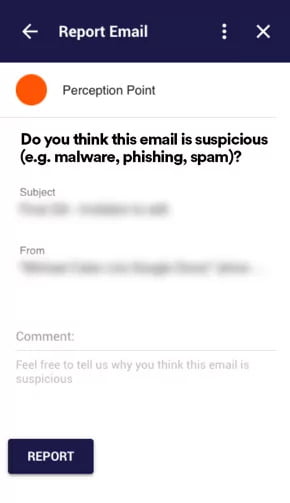
End-user Reporting
TRANSFORMING YOUR EMPLOYEES FROM A SECURITY LOOPHOLE TO AN ACTIVE LINE OF DEFENSE
Advanced impersonation attacks, including BEC, Spear-phishing, see your employees as the weakest link in the chain. Perception Point helps you to change this equation.
Integrated within your employees’ email interface, is a simple button allowing employees to report any suspicious emails directly to our platform. With this new capability, your employees are becoming part of your security stack, helping you in preventing the next attack.
Once an end-user reported a suspicious email, our Incident Response team is being alerted with all relevant data and investigate the potential incident. In the case the email was deemed malicious, you will receive a detailed report and the system will automatically retrieve all similar emails from all relevant email boxes.
Auto-deployment & Updates
Cloud-native platform ensures maximum availability and efficiency.
- Ongoing detection updates
- Direct access to cyber experts
- Research publications
- Enhanced user experience
Support
We don’t take our customers for granted. This is why we are there for you all day, every day.
- Designated customer success engineer
- Ongoing feature requests
- System health management
- Access to our Research team



